4
MARKET OVERVIEW
Identify growth opportunities and strategic gaps in security and vulnerability management.
60
5
INDUSTRY TRENDS
Navigate industry shifts with strategic insights from competitive forces and evolving cybersecurity trends.
71
5.1
PORTER’S FIVE FORCES ANALYSIS
5.1.1
THREAT OF NEW ENTRANTS
5.1.2
THREAT OF SUBSTITUTES
5.1.3
BARGAINING POWER OF SUPPLIERS
5.1.4
BARGAINING POWER OF BUYERS
5.1.5
INTENSITY OF COMPETITIVE RIVALRY
5.2
MACROECONOMIC INDICATORS
5.2.2
GDP TRENDS AND FORECAST
5.2.3
TRENDS IN GLOBAL ICT INDUSTRY
5.2.4
TRENDS IN GLOBAL CYBERSECURITY INDUSTRY
5.3.1
COMPONENT PROVIDERS
5.3.2
TECHNOLOGY PROVIDERS
5.3.3
SECURITY SOLUTION AND SERVICE PROVIDERS
5.3.5
SALES AND DISTRIBUTION
5.5.1
AVERAGE PRICING ANALYSIS OF SOFTWARE, BY SOLUTION, 2025
5.5.2
INDICATIVE PRICING ANALYSIS OF SOFTWARE, BY VENDOR, 2025
5.6
TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
5.7
KEY CONFERENCES AND EVENTS IN 2026
5.8
INVESTMENT AND FUNDING SCENARIO
5.9.1
CASE STUDY 1: INFOSYS RELIES ON QUALYS VMDR FOR BETTER VISIBILITY ACROSS RISKS
5.9.2
CASE STUDY 2: SAI GLOBAL USES RAPID7’S INSIGHTIDR TO PROTECT CLIENT’S HIGHLY SECURE AND REGULATED DATA
5.9.3
CASE STUDY 3: NETWORK INTELLIGENCE CHOSE TRIPWIRE INDUSTRIAL VISIBILITY TO SECURE ITS CRITICAL INFRASTRUCTURE SITES
5.9.4
CASE STUDY 4: QUANTIPHI RELIES ON TENABLE VULNERABILITY MANAGEMENT TO REDUCE CYBER RISK IN CLOUD
5.10
IMPACT OF 2025 US TARIFF – SECURITY AND VULNERABILITY MANAGEMENT MARKET
5.10.3
PRICE IMPACT ANALYSIS
5.10.4
IMPACT ON COUNTRY/REGION
5.10.5
IMPACT ON END-USE INDUSTRIES
6
STRATEGIC DISRUPTIONS: PATENTS, DIGITAL, AND AI ADOPTION
Harness AI-driven innovations to revolutionize vulnerability management and secure future digital landscapes.
93
6.1
KEY EMERGING TECHNOLOGIES
6.1.1
VULNERABILITY ASSESSMENT AND SCANNING
6.1.2
PATCH MANAGEMENT SYSTEMS
6.1.3
CONFIGURATION MANAGEMENT
6.1.4
THREAT AND VULNERABILITY INTELLIGENCE
6.1.5
RISK-BASED VULNERABILITY MANAGEMENT (RBVM)
6.1.6
CONTAINER & CLOUD VULNERABILITY MANAGEMENT
6.1.7
APPLICATION SECURITY (APPSEC) & SAST/DAST/IAST
6.1.8
ENDPOINT VULNERABILITY DETECTION
6.2
COMPLEMENTARY TECHNOLOGIES
6.2.1
SECURITY INFORMATION & EVENT MANAGEMENT (SIEM)
6.2.2
SECURITY ORCHESTRATION, AUTOMATION & RESPONSE (SOAR)
6.2.3
ASSET DISCOVERY & INVENTORY MANAGEMENT (CMDB)
6.2.4
PENETRATION TESTING AND RED TEAM TOOLS
6.2.5
EXPOSURE MANAGEMENT PLATFORMS
6.2.6
REMEDIATION/TICKETING SYSTEMS
6.2.7
DEVSECOPS/CI-CD INTEGRATIONS
6.3
TECHNOLOGY/PRODUCT ROADMAP
6.3.1
SHORT-TERM (2025–2027) | FOUNDATION & EARLY COMMERCIALIZATION
6.3.2
MID-TERM (2027–2030) | EXPANSION & INTEGRATED RISK MANAGEMENT
6.3.3
LONG-TERM (2030–2035+) | AUTONOMOUS & INTELLIGENT EXPOSURE MANAGEMENT
6.5.1
AI-DRIVEN RISK-BASED VULNERABILITY MANAGEMENT (RBVM)
6.5.2
CLOUD & CONTAINER SECURITY AUTOMATION
6.5.3
CONTINUOUS THREAT EXPOSURE MANAGEMENT (CTEM)
6.5.4
QUANTUM-RESILIENT VULNERABILITY MANAGEMENT
6.5.5
AUTONOMOUS REMEDIATION & SECURITY ORCHESTRATION
6.6
IMPACT OF AI/GEN AI ON SECURITY AND VULNERABILITY MANAGEMENT MARKET
6.6.1
BEST PRACTICES IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
6.6.2
CASE STUDIES OF AI IMPLEMENTATION IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
6.6.3
INTERCONNECTED ADJACENT ECOSYSTEMS AND IMPACT ON MARKET PLAYERS
6.6.4
CLIENTS’ READINESS TO ADOPT GENERATIVE AI IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
7
REGULATORY LANDSCAPE
Navigate complex global regulations with a comprehensive guide to regional compliance and industry standards.
107
7.1
REGIONAL REGULATIONS AND COMPLIANCE
7.1.1
REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
8
CONSUMER LANDSCAPE & BUYER BEHAVIOR
Uncover how stakeholder dynamics shape purchasing decisions and reveal critical unmet industry needs.
111
8.1
DECISION-MAKING PROCESS
8.2
BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
8.2.1
KEY STAKEHOLDERS IN BUYING PROCESS
8.3
ADOPTION BARRIERS & INTERNAL CHALLENGES
8.4
UNMET NEEDS FROM VARIOUS END-USE INDUSTRIES
9
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING
Market Size & Growth Rate Forecast Analysis to 2031 in USD Million | 14 Data Tables
116
9.1.1
OFFERING: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
9.2.1
VULNERABILITY ASSESSMENT AND MANAGEMENT
9.2.1.1
IDENTIFY, EVALUATE, PRIORITIZE, AND REMEDIATE SECURITY WEAKNESSES ACROSS THEIR DIGITAL ENVIRONMENTS
9.2.1.2
VULNERABILITY ASSESSMENT AND SCANNING
9.2.1.3
RISK-BASED VULNERABILITY MANAGEMENT
9.2.1.4
OT/IOT VULNERABILITY MANAGEMENT
9.2.2
PATCH AND REMEDIATION MANAGEMENT
9.2.2.1
TRACKING SOFTWARE UPDATES AND CONFIGURATION CHANGES ACROSS ORGANIZATION’S DIGITAL ASSETS
9.2.3
ASSET DISCOVERY AND INVENTORY MANAGEMENT
9.2.3.1
AUTOMATICALLY IDENTIFY DEVICES, WORKLOADS, AND APPLICATIONS CONNECTED TO NETWORK AND MAINTAIN REAL-TIME INVENTORY
9.2.4
CONFIGURATION AND COMPLIANCE
9.2.4.1
ENSURING CONFIGURATION ACCORDING TO DEFINED SECURITY BASELINES
9.3.1
PROFESSIONAL SERVICES
9.3.1.1
PROFESSIONAL SERVICES OFFER EXPERT TEAM SUPPORT AND DEDICATED PROJECT CONSULTANCY FOR DEPLOYMENT
9.3.1.2
CONSULTING AND ADVISORY SERVICES
9.3.1.3
INTEGRATION SERVICES
9.3.1.4
SUPPORT AND MAINTENANCE
9.3.2.1
MANAGED SERVICES ENSURE EXPERT TECHNICAL SUPPORT FOR SEAMLESS INTEGRATION AND OPERATION OF SECURITY AND VULNERABILITY MANAGEMENT
9.3.2.2
MANAGED VULNERABILITY SCANNING
9.3.2.3
MANAGED PATCH AND REMEDIATION
9.3.2.4
CONTINUOUS MONITORING & REPORTING
10
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE
Market Size & Growth Rate Forecast Analysis to 2031 in USD Million | 6 Data Tables
128
10.1.1
DEPLOYMENT MODE: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
10.2.1
ON-PREMISE SOLUTIONS PROVIDE ORGANIZATIONS WITH FULL CONTROL OVER ALL PLATFORMS
10.3.1
CLOUD DEPLOYMENT BENEFICIAL FOR ORGANIZATIONS WITH LIMITED SECURITY BUDGETS
11
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE
Market Size & Growth Rate Forecast Analysis to 2031 in USD Million | 10 Data Tables
133
11.1.1
SECURITY TYPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
11.2.1
INCREASING NEED TO IDENTIFY RISKS ON DEVICES TO PREVENT UNAUTHORIZED ACCESS
11.3.1
VULNERABILITY MANAGEMENT IMPROVES NETWORK SECURITY BY REDUCING ATTACK SURFACE
11.4
APPLICATION SECURITY
11.4.1
APPLICATION SECURITY PROTECTS USER PRIVACY, UPHOLDS TRUST, AND ASSURES BUSINESS CONTINUITY
11.5.1
EFFICIENT VULNERABILITY MANAGEMENT VITAL TO PRESERVE INTEGRITY, AVAILABILITY, AND CONFIDENTIALITY OF CLOUD-BASED ASSETS
12
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET
Market Size & Growth Rate Forecast Analysis to 2031 in USD Million | 10 Data Tables
140
12.1.1
TARGET: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
12.2.1
EFFECTIVE VULNERABILITY MANAGEMENT FOR IT INFRASTRUCTURE COMBINES AUTOMATED DISCOVERY, RISK-BASED PRIORITIZATION, AND CONTINUOUS MONITORING
12.3
CONTENT MANAGEMENT VULNERABILITIES
12.3.1
RISE IN AMOUNT OF CONTENT GENERATED IN INTER- AND INTRA-ORGANIZATIONS DUE TO DIGITALIZATION
12.4.1
VULNERABILITY MANAGEMENT HELPS MITIGATE RISKS BY CONTINUOUSLY SCANNING IOT NETWORKS
12.5.1
INCREASING CYBERATTACKS ON APIS TO DRIVE ADOPTION OF SECURITY AND VULNERABILITY MANAGEMENT SOLUTIONS
12.6
OTHER TARGET VULNERABILITIES
13
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL
Market Size & Growth Rate Forecast Analysis to 2031 in USD Million | 20 Data Tables
147
13.1.1
VERTICAL: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
13.2.1
BFSI VERTICAL PRIORITIZES CUSTOMER PRIVACY AND SECURITY, ONLINE TRANSACTIONS, AND SENSITIVE INFORMATION
13.3.1
HEALTHCARE SECTOR SECURES PERSONAL HEALTH INFORMATION AND CRITICAL DATA ABOUT PATIENTS
13.4.1
VULNERABILITY MANAGEMENT HELPS GOVERNMENT AGENCIES COMPLY WITH STRICT CYBERSECURITY LAWS
13.5.1
TECHNOLOGICAL ADVANCEMENTS IN MANUFACTURING VERTICAL TO DRIVE DEMAND FOR VULNERABILITY MANAGEMENT
13.6.1
ENERGY COMPANIES FACE HIGHER RISKS OF CYBERATTACKS DISRUPTING POWER DISTRIBUTION, INCREASING SECURITY DEMAND
13.7.1
IT ORGANIZATIONS HANDLE SIGNIFICANT SENSITIVE DATA AND CRITICAL OPERATIONS FOR GLOBAL CLIENTS, REQUIRING ADVANCED SECURITY SOLUTIONS
13.8.1
INCREASING ATTACK SURFACE IN RETAIL SECTOR DUE TO WIDESPREAD USE OF INTERNET AND SMARTPHONES
13.9.1
VULNERABILITY SOLUTIONS LIKE THREAT INTELLIGENCE INTEGRATION OFFER TELECOM OPERATORS REAL-TIME INSIGHTS INTO EMERGING CYBER THREATS
13.10
TRAVEL & HOSPITALITY
13.10.1
SECURITY SOLUTIONS SAFEGUARD TRAVEL INDUSTRY NETWORKS, ENSURING CONTINUOUS AND SECURE CLIENT SERVICES
14
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION
Comprehensive coverage of 8 Regions with country-level deep-dive of 18 Countries | 504 Data Tables.
160
14.2.1
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
14.2.2.1
STRONG PRESENCE OF SECURITY AND VULNERABILITY MANAGEMENT VENDORS TO DRIVE MARKET
14.2.3.1
INCREASE IN ONLINE FRAUD AND MALICIOUS ATTACKS TO DRIVE MARKET
14.3.1
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
14.3.2.1
INCREASE IN INVESTMENTS IN CYBER DEFENSE TO DRIVE MARKET
14.3.3.1
ADVANCEMENT TOWARDS DIGITALIZATION ACROSS ALL BUSINESS AREAS TO DRIVE MARKET
14.3.4.1
INCREASING GOVERNMENT INITIATIVES AND SUPPORT TO DRIVE MARKET
14.3.5.1
INCREASING CYBERATTACKS DUE TO RAPID DIGITALIZATION TO DRIVE MARKET
14.3.6.1
INCREASING DEMAND FOR SECURITY AND VULNERABILITY MANAGEMENT SOLUTIONS DUE TO RISING CYBER TERRORISM THREATS TO DRIVE MARKET
14.3.7.1
DEALS AND INITIATIVES TO ENHANCE SECURITY AND VULNERABILITY MANAGEMENT LANDSCAPE TO DRIVE MARKET
14.4.1
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
14.4.2.1
INCREASING INVESTMENTS IN ADVANCED TOOLS FOR SECURITY AND VULNERABILITY MANAGEMENT TO DRIVE MARKET
14.4.3.1
NEED FOR ADVANCED SECURITY AND VULNERABILITY MANAGEMENT SOLUTIONS TO MINIMIZE ATTACK SURFACES TO DRIVE MARKET
14.4.4.1
INCREASING COMPLEXITY OF CYBER THREATS TO DRIVE MARKET
14.4.5.1
INCREASING AWARENESS AND DEMAND FOR SECURITY AND VULNERABILITY MANAGEMENT SOLUTIONS AND SERVICES TO DRIVE MARKET
14.4.6.1
RISING ADOPTION OF INTERNET-ENABLED PRODUCTS TO DRIVE MARKET
14.4.7
REST OF ASIA PACIFIC
14.5
MIDDLE EAST & AFRICA
14.5.1
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
14.5.2.1
INCREASE IN CYBER THREATS AND REGULATORY DEMANDS DRIVING GROWTH OF MARKET
14.5.3.1
RISE IN GOVERNMENT INITIATIVES TO REDUCE CYBERSECURITY ATTACKS TO DRIVE MARKET
14.5.3.4
REST OF GCC COUNTRIES
14.5.4
REST OF MIDDLE EAST
14.5.5.1
INCREASE IN CYBERATTACKS DUE TO GROWING INTERNET PENETRATION TO DRIVE MARKET
14.5.6.1
SOUTH AFRICA’S DIGITAL REVOLUTION TRANSFORMING ITS ECONOMY AT RECORD PACE
14.6.1
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET DRIVERS
14.6.2.1
INCREASE IN HACKING INCIDENTS DUE TO RISE IN DIGITAL PENETRATION TO DRIVE MARKET
14.6.3.1
INCREASE IN ADOPTION OF CLOUD-BASED SERVICES AND BROADBAND TO DRIVE MARKET
14.6.4
REST OF LATIN AMERICA
15
COMPETITIVE LANDSCAPE
Uncover key player strategies and market shifts shaping competitive dynamics and valuation in 2024.
335
15.2
KEY PLAYER STRATEGIES/RIGHT TO WIN
15.3
REVENUE ANALYSIS, 2020–2024
15.4
COMPANY VALUATION AND FINANCIAL METRICS
15.5
MARKET SHARE ANALYSIS, 2024
15.7
COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
15.7.5
COMPANY FOOTPRINT: KEY PLAYERS, 2024
15.7.5.1
COMPANY FOOTPRINT
15.7.5.2
REGION FOOTPRINT
15.7.5.3
SOLUTION FOOTPRINT
15.7.5.4
DEPLOYMENT MODE FOOTPRINT
15.7.5.5
VERTICAL FOOTPRINT
15.8
COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
15.8.1
PROGRESSIVE COMPANIES
15.8.2
RESPONSIVE COMPANIES
15.8.5
COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
15.8.5.1
DETAILED LIST OF KEY STARTUPS/SMES
15.8.5.2
COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
15.9
COMPETITIVE SCENARIO
15.9.1
PRODUCT LAUNCHES AND ENHANCEMENTS
16
COMPANY PROFILES
In-depth Company Profiles of Leading Market Players with detailed Business Overview, Product and Service Portfolio, Recent Developments, and Unique Analyst Perspective (MnM View)
359
16.1.1.1
BUSINESS OVERVIEW
16.1.1.2
PRODUCTS/SOLUTIONS/SERVICES OFFERED
16.1.1.3
RECENT DEVELOPMENTS
17
RESEARCH METHODOLOGY
411
17.1.2.1
BREAKUP OF PRIMARY PROFILES
17.1.2.2
KEY INDUSTRY INSIGHTS
17.3
MARKET SIZE ESTIMATION
17.3.2
BOTTOM-UP APPROACH
17.5
RESEARCH ASSUMPTIONS
17.6
RESEARCH LIMITATIONS
18.2
KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
18.3
CUSTOMIZATION OPTIONS
TABLE 1
USD EXCHANGE RATES, 2019–2024
TABLE 2
UNMET NEEDS AND WHITE SPACES IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
TABLE 3
STRATEGIC MOVES BY PLAYERS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
TABLE 4
PORTER’S FIVE FORCES IMPACT ANALYSIS
TABLE 5
GDP PERCENTAGE CHANGE, BY KEY COUNTRY, 2021–2030
TABLE 6
SECURITY AND VULNERABILITY MANAGEMENT MARKET: ECOSYSTEM
TABLE 7
SECURITY AND VULNERABILITY MANAGEMENT MARKET: AVERAGE SELLING PRICE OF SOLUTIONS, BY KEY PLAYER, 2025
TABLE 8
SECURITY AND VULNERABILITY MANAGEMENT MARKET: INDICATIVE PRICING ANALYSIS OF SOLUTIONS
TABLE 9
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DETAILED LIST OF KEY CONFERENCES AND EVENTS, 2026
TABLE 10
KEY TARIFF RATES
TABLE 11
LIST OF TOP PATENTS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET, 2023–2025
TABLE 12
TOP USE CASES AND MARKET POTENTIAL
TABLE 13
BEST PRACTICES: USE CASES
TABLE 14
SECURITY AND VULNERABILITY MANAGEMENT MARKET: CASE STUDIES RELATED TO GEN AI IMPLEMENTATION
TABLE 15
INTERCONNECTED ADJACENT ECOSYSTEMS AND IMPACT ON MARKET PLAYERS
TABLE 16
NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 17
EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 18
ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 19
MIDDLE EAST & AFRICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 20
LATIN AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 21
GLOBAL INDUSTRY STANDARDS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
TABLE 22
INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS (%)
TABLE 23
KEY BUYING CRITERIA FOR TOP THREE VERTICALS
TABLE 24
UNMET NEEDS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY END-USE INDUSTRY
TABLE 25
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 26
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 27
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 28
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 29
SOLUTION: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 30
SOLUTION: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 31
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 32
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 33
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 34
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 35
SERVICES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 36
SERVICES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 37
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 38
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 39
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 40
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 41
ON-PREMISES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 42
ON-PREMISES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 43
CLOUD: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 44
CLOUD: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 45
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 46
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 47
ENDPOINT SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 48
ENDPOINT SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 49
NETWORK SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 50
NETWORK SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 51
APPLICATION SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 52
APPLICATION SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 53
CLOUD SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 54
CLOUD SECURITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 55
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 56
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 57
IT INFRASTRUCTURE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 58
IT INFRASTRUCTURE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 59
CONTENT MANAGEMENT VULNERABILITIES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 60
CONTENT MANAGEMENT VULNERABILITIES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 61
IOT VULNERABILITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 62
IOT VULNERABILITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 63
API VULNERABILITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 64
API VULNERABILITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 65
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 66
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 67
BFSI: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 68
BFSI: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 69
HEALTHCARE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 70
HEALTHCARE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 71
GOVERNMENT: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 72
GOVERNMENT: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 73
MANUFACTURING: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 74
MANUFACTURING: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 75
ENERGY & UTILITIES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 76
ENERGY & UTILITIES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 77
IT & ITES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 78
IT & ITES: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 79
RETAIL & E-COMMERCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 80
RETAIL & E-COMMERCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 81
TELECOMMUNICATIONS: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 82
TELECOMMUNICATIONS: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 83
TRAVEL & HOSPITALITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 84
TRAVEL & HOSPITALITY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 85
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 86
SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 87
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 88
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 89
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 90
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 91
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 92
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 93
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 94
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 95
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 96
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 97
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 98
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 99
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 100
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 101
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 102
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 103
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 104
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 105
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 106
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 107
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 108
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 109
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 110
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 111
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 112
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 113
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 114
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 115
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 116
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 117
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 118
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 119
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 120
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 121
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 122
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 123
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 124
US: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 125
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 126
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 127
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 128
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 129
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 130
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 131
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 132
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 133
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 134
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 135
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 136
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 137
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 138
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 139
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 140
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 141
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 142
CANADA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 143
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 144
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 145
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 146
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 147
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 148
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 149
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 150
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 151
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 152
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 153
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 154
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 155
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 156
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 157
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 158
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 159
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 160
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 161
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 162
EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 163
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 164
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 165
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 166
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 167
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 168
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 169
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 170
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 171
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 172
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 173
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 174
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 175
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 176
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 177
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 178
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 179
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 180
UK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 181
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 182
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 183
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 184
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 185
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 186
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 187
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 188
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 189
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 190
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 191
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 192
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 193
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 194
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 195
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 196
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 197
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 198
GERMANY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 199
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 200
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 201
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 202
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 203
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 204
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 205
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 206
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 207
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 208
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 209
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 210
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 211
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 212
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 213
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 214
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 215
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 216
FRANCE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 217
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 218
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 219
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 220
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 221
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 222
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 223
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 224
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 225
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 226
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 227
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 228
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 229
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 230
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 231
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 232
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 233
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 234
ITALY: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 235
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 236
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 237
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 238
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 239
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 240
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 241
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 242
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 243
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 244
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 245
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 246
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 247
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 248
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 249
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 250
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 251
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 252
SWEDEN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 253
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 254
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 255
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 256
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 257
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 258
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 259
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 260
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 261
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 262
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 263
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 264
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 265
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 266
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 267
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 268
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 269
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 270
DENMARK: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 271
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 272
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 273
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 274
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 275
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 276
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 277
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 278
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 279
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 280
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 281
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 282
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 283
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 284
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 285
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 286
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 287
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 288
REST OF EUROPE: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 289
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 290
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 291
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 292
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 293
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 294
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 295
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 296
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 297
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 298
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 299
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 300
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 301
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 302
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 303
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 304
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 305
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 306
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 307
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 308
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 309
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 310
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 311
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 312
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 313
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 314
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 315
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 316
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 317
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 318
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 319
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 320
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 321
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 322
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 323
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 324
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 325
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 326
CHINA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 327
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 328
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 329
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 330
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 331
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 332
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 333
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 334
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 335
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 336
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 337
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 338
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 339
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 340
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 341
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 342
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 343
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 344
JAPAN: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 345
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 346
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 347
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 348
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 349
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 350
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 351
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 352
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 353
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 354
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 355
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 356
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 357
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 358
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 359
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 360
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 361
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 362
INDIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 363
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 364
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 365
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 366
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 367
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 368
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 369
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 370
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 371
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 372
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 373
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 374
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 375
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 376
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 377
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 378
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 379
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 380
AUSTRALIA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 381
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 382
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 383
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 384
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 385
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 386
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 387
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 388
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 389
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 390
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 391
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 392
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 393
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 394
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 395
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 396
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 397
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 398
SOUTH KOREA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 399
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 400
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 401
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 402
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 403
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 404
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 405
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 406
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 407
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 408
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 409
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 410
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 411
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 412
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 413
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 414
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 415
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 416
REST OF ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 417
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 418
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 419
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 420
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 421
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 422
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 423
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 424
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 425
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 426
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 427
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 428
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 429
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 430
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 431
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 432
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 433
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 434
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 435
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2019–2024 (USD MILLION)
TABLE 436
MIDDLE EAST & AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY REGION, 2025–2031 (USD MILLION)
TABLE 437
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 438
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 439
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 440
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 441
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 442
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 443
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 444
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 445
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 446
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 447
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 448
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 449
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 450
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 451
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 452
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 453
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 454
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 455
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 456
MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 457
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 458
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 459
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 460
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 461
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 462
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 463
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 464
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 465
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 466
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 467
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 468
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 469
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 470
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 471
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 472
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 473
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 474
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 475
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 476
GCC: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 477
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 478
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 479
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 480
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 481
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 482
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 483
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 484
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 485
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 486
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 487
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 488
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 489
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 490
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 491
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 492
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 493
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 494
REST OF MIDDLE EAST: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 495
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 496
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 497
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 498
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 499
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 500
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 501
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 502
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 503
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 504
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 505
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 506
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 507
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 508
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 509
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 510
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 511
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 512
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 513
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 514
AFRICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 515
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 516
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 517
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 518
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 519
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 520
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 521
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 522
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 523
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 524
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 525
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 526
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 527
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 528
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 529
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 530
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 531
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 532
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 533
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2019–2024 (USD MILLION)
TABLE 534
LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY COUNTRY, 2025–2031 (USD MILLION)
TABLE 535
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 536
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 537
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 538
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 539
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 540
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 541
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 542
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 543
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 544
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 545
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 546
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 547
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 548
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 549
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 550
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 551
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 552
BRAZIL: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 553
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 554
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 555
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 556
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 557
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 558
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 559
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 560
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 561
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 562
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 563
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 564
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 565
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 566
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 567
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 568
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 569
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 570
MEXICO: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 571
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2019–2024 (USD MILLION)
TABLE 572
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY OFFERING, 2025–2031 (USD MILLION)
TABLE 573
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2019–2024 (USD MILLION)
TABLE 574
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SOLUTION, 2025–2031 (USD MILLION)
TABLE 575
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2019–2024 (USD MILLION)
TABLE 576
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VULNERABILITY ASSESSMENT AND MANAGEMENT, 2025–2031 (USD MILLION)
TABLE 577
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2019–2024 (USD MILLION)
TABLE 578
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SERVICE, 2025–2031 (USD MILLION)
TABLE 579
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019–2024 (USD MILLION)
TABLE 580
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025–2031 (USD MILLION)
TABLE 581
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019–2024 (USD MILLION)
TABLE 582
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025–2031 (USD MILLION)
TABLE 583
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2019–2024 (USD MILLION)
TABLE 584
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY SECURITY TYPE, 2025–2031 (USD MILLION)
TABLE 585
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2019–2024 (USD MILLION)
TABLE 586
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY TARGET, 2025–2031 (USD MILLION)
TABLE 587
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2019–2024 (USD MILLION)
TABLE 588
REST OF LATIN AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET, BY VERTICAL, 2025–2031 (USD MILLION)
TABLE 589
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DEGREE OF COMPETITION
TABLE 590
SECURITY AND VULNERABILITY MANAGEMENT MARKET: REGION FOOTPRINT
TABLE 591
SECURITY AND VULNERABILITY MANAGEMENT MARKET: SOLUTION FOOTPRINT
TABLE 592
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DEPLOYMENT MODE FOOTPRINT
TABLE 593
SECURITY AND VULNERABILITY MANAGEMENT MARKET: VERTICAL FOOTPRINT
TABLE 594
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DETAILED LIST OF KEY STARTUPS/SMES
TABLE 595
SECURITY AND VULNERABILITY MANAGEMENT MARKET: SOLUTION FOOTPRINT OF KEY STARTUPS/SMES
TABLE 596
SECURITY AND VULNERABILITY MANAGEMENT MARKET: VERTICAL FOOTPRINT OF KEY STARTUPS/SMES
TABLE 597
SECURITY AND VULNERABILITY MANAGEMENT MARKET: REGIONAL FOOTPRINT OF KEY STARTUPS/SMES
TABLE 598
SECURITY AND VULNERABILITY MANAGEMENT MARKET: PRODUCT LAUNCHES AND ENHANCEMENTS, 2023–OCTOBER 2025
TABLE 599
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DEALS, 2023–OCTOBER 2025
TABLE 600
MICROSOFT: COMPANY OVERVIEW
TABLE 601
MICROSOFT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 602
MICROSOFT: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 603
TENABLE: COMPANY OVERVIEW
TABLE 604
TENABLE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 605
TENABLE: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 607
CISCO: COMPANY OVERVIEW
TABLE 608
CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 610
CHECK POINT: COMPANY OVERVIEW
TABLE 611
CHECK POINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 612
CHECK POINT: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 613
CHECK POINT: DEALS
TABLE 614
IBM: COMPANY OVERVIEW
TABLE 615
IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 616
IBM: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 618
IBM: OTHER DEVELOPMENTS
TABLE 619
CROWDSTRIKE: COMPANY OVERVIEW
TABLE 620
CROWDSTRIKE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 621
CROWDSTRIKE: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 622
CROWDSTRIKE: DEALS
TABLE 623
RAPID7: COMPANY OVERVIEW
TABLE 624
RAPID7: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 625
RAPID7: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 627
FORTRA: COMPANY OVERVIEW
TABLE 628
FORTRA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 629
FORTRA: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 630
QUALYS: COMPANY OVERVIEW
TABLE 631
QUALYS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 632
QUALYS: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 634
SERVICENOW: COMPANY OVERVIEW
TABLE 635
SERVICENOW: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 636
SERVICENOW: PRODUCT LAUNCHES/ENHANCEMENTS
TABLE 637
SERVICENOW: DEALS
TABLE 638
FACTOR ANALYSIS
FIGURE 1
KEY INSIGHTS & MARKET HIGHLIGHTS
FIGURE 2
GLOBAL SECURITY AND VULNERABILITY MANAGEMENT MARKET, 2025–2031
FIGURE 3
MAJOR STRATEGIES ADOPTED BY KEY PLAYERS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET (2020-2025)
FIGURE 4
DISRUPTIVE TRENDS IMPACTING GROWTH OF SECURITY AND VULNERABILITY MANAGEMENT MARKET
FIGURE 5
HIGH-GROWTH SEGMENTS AND EMERGING FRONTIERS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET, 2025
FIGURE 6
ASIA PACIFIC TO REGISTER FASTEST GROWTH DURING FORECAST PERIOD
FIGURE 7
TECHNOLOGICAL ADVANCEMENTS AND STRINGENT DATA PROTECTION TO DRIVE DEMAND FOR SECURITY AND VULNERABILITY MANAGEMENT
FIGURE 8
SOLUTIONS SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE
FIGURE 9
VULNERABILITY ASSESSMENT AND MANAGEMENT SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE
FIGURE 10
VULNERABILITY ASSESSMENT AND SCANNING SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE
FIGURE 11
PROFESSIONAL SERVICES SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE
FIGURE 12
DESIGN AND ADVISORY SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE
FIGURE 13
CLOUD DEPLOYMENT SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE
FIGURE 14
ENDPOINT SECURITY SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE
FIGURE 15
IT INFRASTRUCTURE SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE
FIGURE 16
BFSI TO ACCOUNT FOR LARGEST MARKET SHARE
FIGURE 17
ASIA PACIFIC TO EMERGE AS BEST MARKET FOR INVESTMENT IN NEXT FIVE YEARS
FIGURE 18
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
FIGURE 19
NUMBER OF COMMON IT SECURITY VULNERABILITIES AND EXPOSURES (CVES) WORLDWIDE, 2009–2024
FIGURE 20
AVERAGE COST OF DATA BREACH, 2014–2023 (USD MILLION)
FIGURE 21
SECURITY AND VULNERABILITY MANAGEMENT MARKET: PORTER’S FIVE FORCES ANALYSIS
FIGURE 22
SECURITY AND VULNERABILITY MANAGEMENT MARKET: VALUE CHAIN ANALYSIS
FIGURE 23
SECURITY AND VULNERABILITY MANAGEMENT MARKET: ECOSYSTEM
FIGURE 24
AVERAGE PRICING ANALYSIS OF SOFTWARE, BY SOLUTION, 2025
FIGURE 25
TRENDS/DISRUPTIONS INFLUENCING CUSTOMER BUSINESS
FIGURE 26
LEADING GLOBAL SECURITY AND VULNERABILITY MANAGEMENT STARTUPS AND SMES, BY NUMBER OF INVESTORS AND FUNDING ROUNDS, 2021–2025
FIGURE 27
PATENTS GRANTED IN SECURITY AND VULNERABILITY MANAGEMENT MARKET, 2015–2025
FIGURE 28
REGIONAL ANALYSIS OF PATENTS GRANTED IN SECURITY AND VULNERABILITY MANAGEMENT MARKET
FIGURE 29
FUTURE APPLICATIONS OF SECURITY AND VULNERABILITY MANAGEMENT
FIGURE 30
SECURITY AND VULNERABILITY MANAGEMENT MARKET: DECISION-MAKING FACTORS
FIGURE 31
INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
FIGURE 32
KEY BUYING CRITERIA FOR TOP THREE VERTICALS
FIGURE 33
ADOPTION BARRIERS AND INTERNAL CHALLENGES
FIGURE 34
SOLUTIONS SEGMENT TO LEAD MARKET FROM 2025 TO 2031
FIGURE 35
VULNERABILITY ASSESSMENT & MANAGEMENT SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
FIGURE 36
PROFESSIONAL SERVICES SEGMENT TO LEAD MARKET FROM 2025 TO 2030
FIGURE 37
CLOUD SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
FIGURE 38
CLOUD SECURITY SEGMENT TO LEAD MARKET FROM 2025 TO 2031
FIGURE 39
IT INFRASTRUCTURE SEGMENT TO LEAD MARKET IN 2025
FIGURE 40
BFSI SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
FIGURE 41
NORTH AMERICA TO BE LARGEST MARKET DURING FORECAST PERIOD
FIGURE 42
NORTH AMERICA: SECURITY AND VULNERABILITY MANAGEMENT MARKET SNAPSHOT
FIGURE 43
ASIA PACIFIC: SECURITY AND VULNERABILITY MANAGEMENT MARKET SNAPSHOT
FIGURE 44
SEGMENTAL REVENUE ANALYSIS OF KEY MARKET PLAYERS, 2020–2024 (USD MILLION)
FIGURE 45
SECURITY AND VULNERABILITY MANAGEMENT MARKET: COMPANY VALUATION OF KEY VENDORS (USD BILLION)
FIGURE 46
SECURITY AND VULNERABILITY MANAGEMENT MARKET: FINANCIAL METRICS
FIGURE 47
SHARE OF LEADING COMPANIES IN SECURITY AND VULNERABILITY MANAGEMENT MARKET, 2024 (%)
FIGURE 48
SECURITY AND VULNERABILITY MANAGEMENT MARKET: COMPARISON OF VENDOR BRANDS
FIGURE 49
SECURITY AND VULNERABILITY MANAGEMENT MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
FIGURE 50
SECURITY AND VULNERABILITY MANAGEMENT MARKET: COMPANY FOOTPRINT
FIGURE 51
SECURITY AND VULNERABILITY MANAGEMENT MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
FIGURE 52
MICROSOFT: COMPANY SNAPSHOT
FIGURE 53
TENABLE: COMPANY SNAPSHOT
FIGURE 54
CISCO: COMPANY SNAPSHOT
FIGURE 55
CHECK POINT: COMPANY SNAPSHOT
FIGURE 56
IBM: COMPANY SNAPSHOT
FIGURE 57
CROWDSTRIKE: COMPANY SNAPSHOT
FIGURE 58
RAPID7: COMPANY SNAPSHOT
FIGURE 59
QUALYS: COMPANY SNAPSHOT
FIGURE 60
SERVICENOW: COMPANY SNAPSHOT
FIGURE 61
SECURITY AND VULNERABILITY MANAGEMENT MARKET: RESEARCH DESIGN
FIGURE 62
SECURITY AND VULNERABILITY MANAGEMENT MARKET: TOP-DOWN APPROACH
FIGURE 63
SECURITY AND VULNERABILITY MANAGEMENT MARKET: BOTTOM-UP APPROACH
FIGURE 64
APPROACH 1 (SUPPLY SIDE): REVENUE FROM SOLUTIONS/SERVICES OF SECURITY AND VULNERABILITY MANAGEMENT VENDORS
FIGURE 65
APPROACH 1: SUPPLY-SIDE ANALYSIS
FIGURE 66
SECURITY AND VULNERABILITY MANAGEMENT MARKET ESTIMATION: RESEARCH FLOW
FIGURE 67
COLLECTIVE REVENUE FROM ALL SOLUTIONS IN SECURITY AND VULNERABILITY MANAGEMENT MARKET: APPROACH 2, BOTTOM-UP (SUPPLY SIDE)
FIGURE 68
APPROACH 2, BOTTOM-UP (DEMAND SIDE): SOLUTIONS/SERVICES





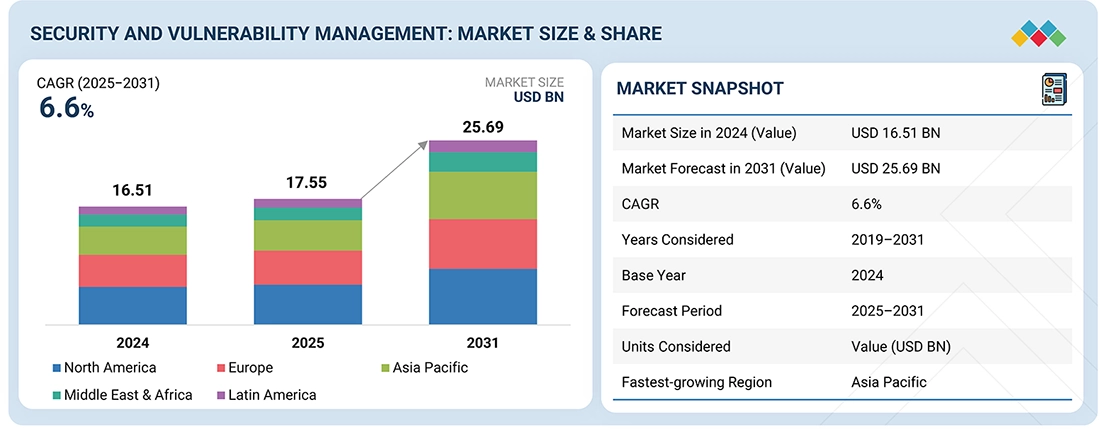
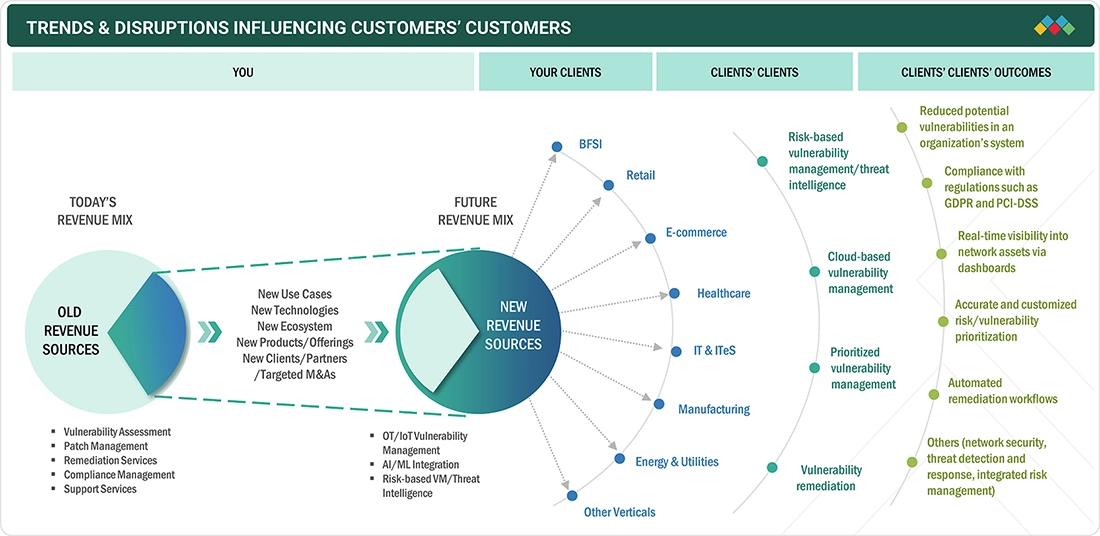






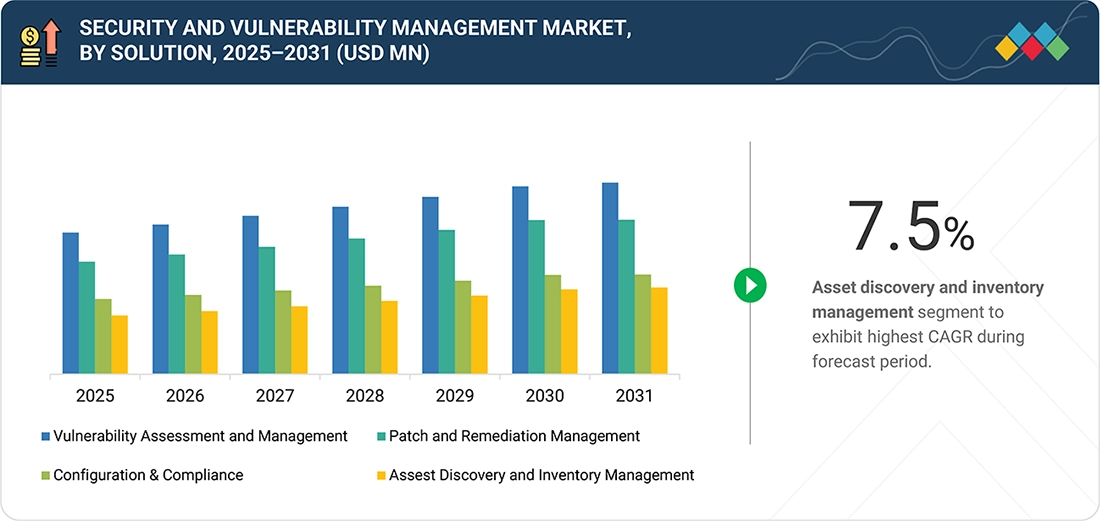

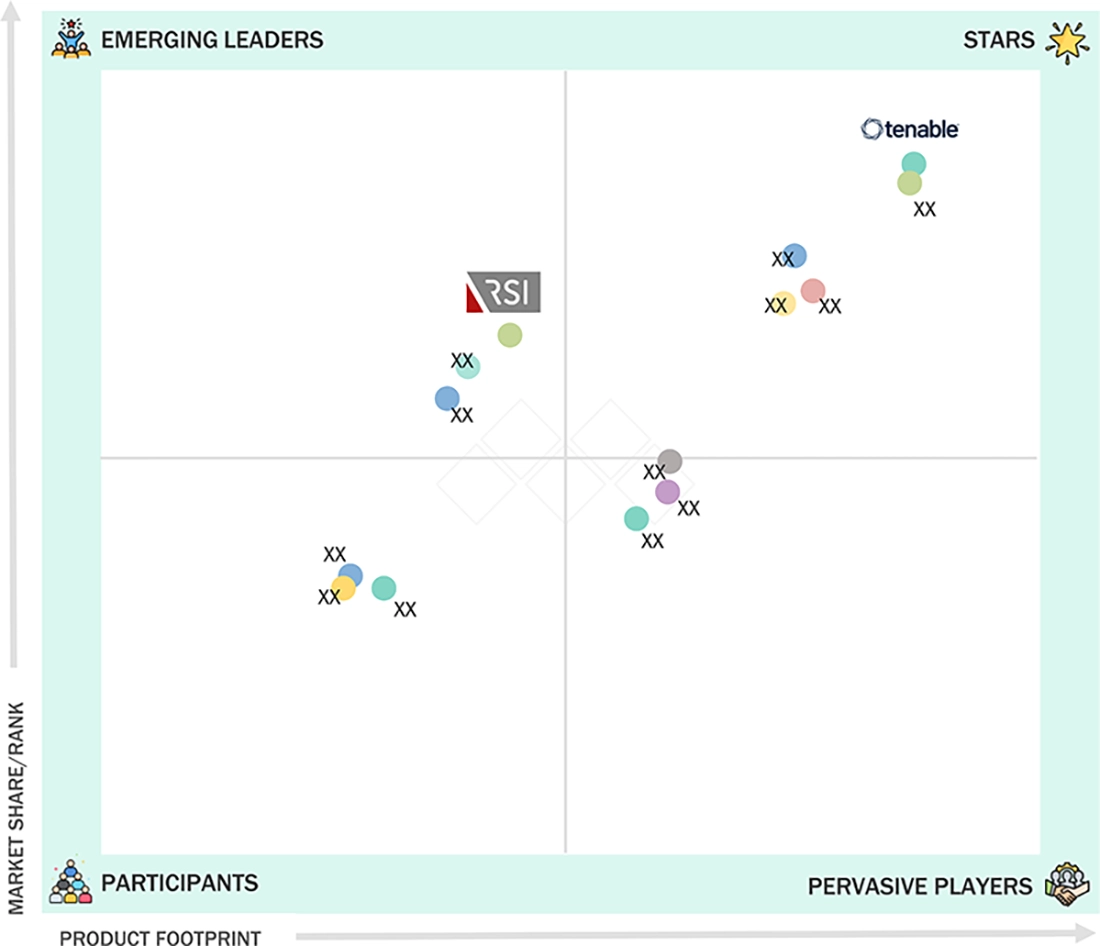
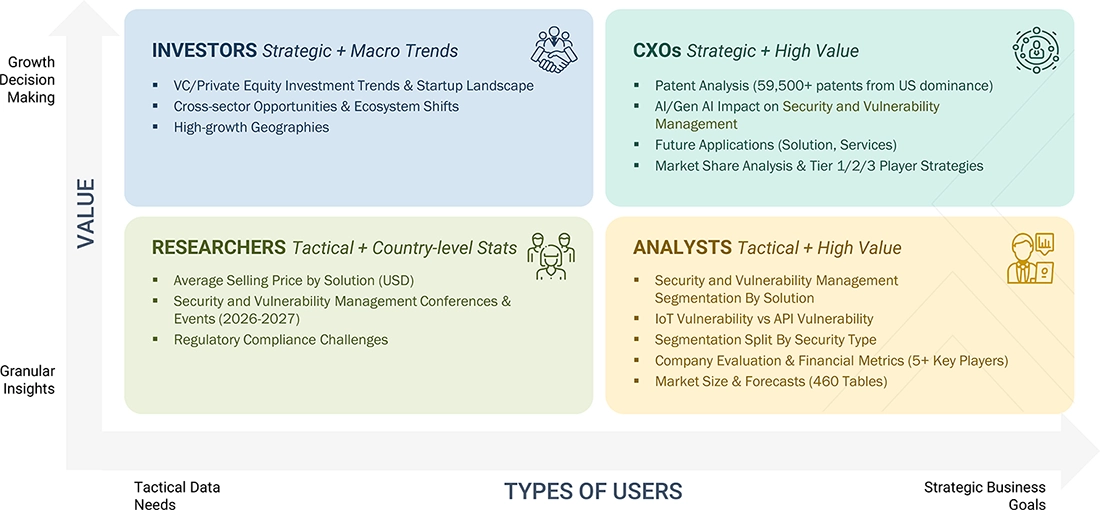

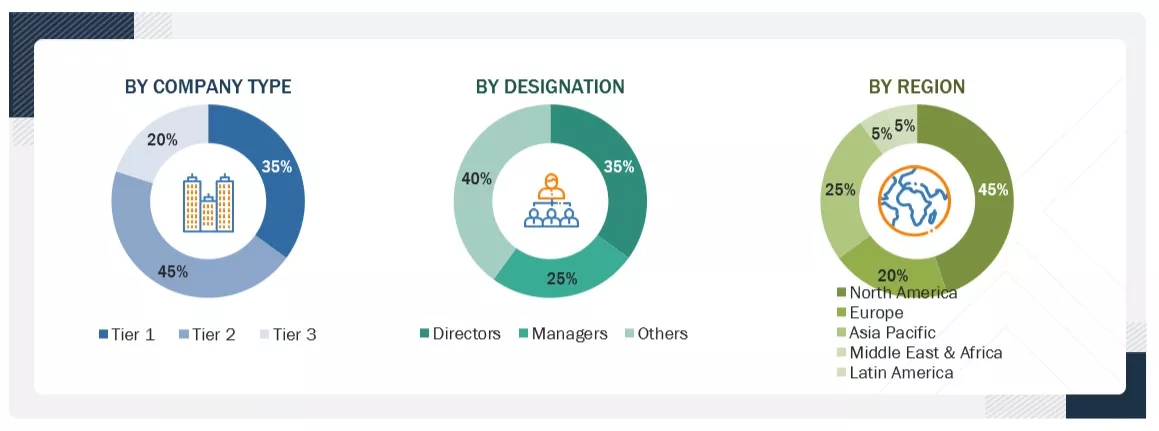
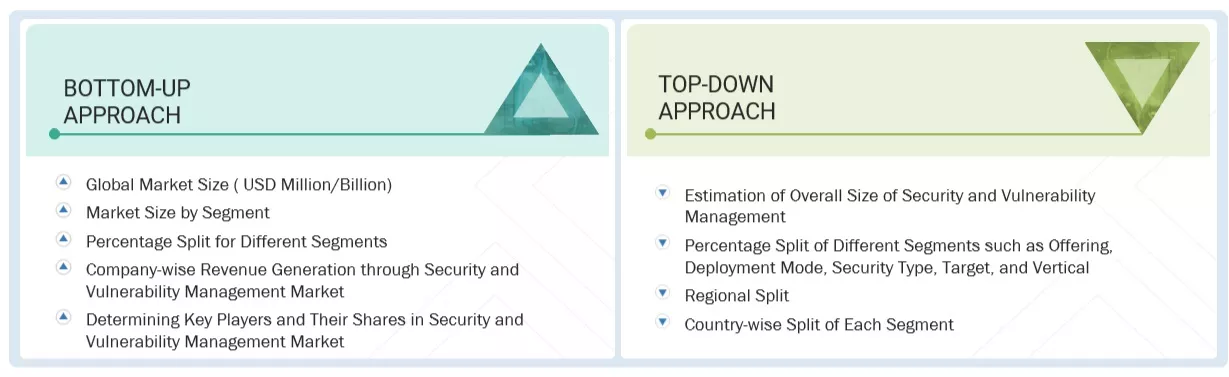












Growth opportunities and latent adjacency in Security & Vulnerability Management (SVM) Market